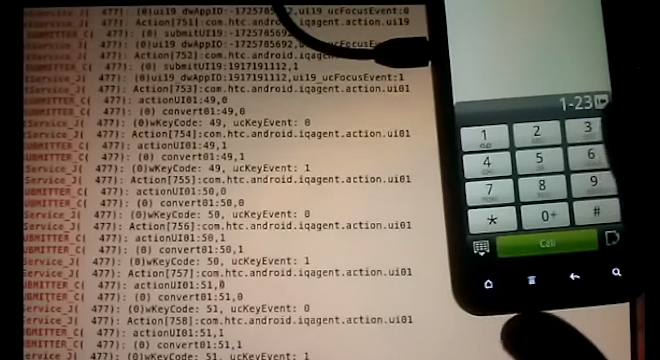
Mobile phone intelligence company Carrier IQ’s self-named tracking software doesn’t record the contents of a user’s data and is being unfairly targeted by the media and hysterical users, according to several security researchers who have conducted further analysis on the software.
“It records the fact that a keystroke occurs, not the specific key the user entered,” Becky Bace, a former National Security Agency computer engineer and founder and CEO of security consulting firm Infidel, Inc., told TPM via email. “Any keystrokes monitored are limited to the user interactions with the numeric keypad, not the alphanumeric keyboard, and are filtered on input for specific sequences that trigger specific diagnostic actions.”
Bace was earlier cited by Carrier IQ in its updated statement defending the software on Friday.
Bace told TPM she began investigating the software after Carrier IQ’s CEO Larry Lenhart asked for advice after another Android researcher posted a seemingly incriminating video demonstration of Carrier IQ’s capabilities on Monday.
Bace acknowledged to TPM that while she and Lenhart are longtime friends, “My defense of them is motivated by outrage that a good technology firm serving a critical, legitimate need should be victimized on the altar of privacy concerns, especially when such concerns appear, on reasonable inspection, to be unfounded.”
Other security experts have stepped up to explain that the software is benign as well.
“The Carrier IQ app simply doesn’t meet the requirements in terms of functionality or intent to be classified as a ‘keylogger,'” Jon Oberheide, a co-founder of Ann Arbor, Mich.-based Duo Security, said in an e-mail to CRN News.
“The application does not record and transmit keystroke data back to carriers,” Dan Rosenberg, a security consultant at Virtual Security Research, told CNET on Friday. “They’re not recording keystroke information, they’re using keystroke events as part of the application.”
Rosenberg sounded the alarm earlier in the week, but to no avail.
“After reverse engineering CarrierIQ myself, I have seen no evidence that they are collecting anything more than what they’ve publicly claimed: anonymized metrics data,” Rosenberg wrote in a post on Pastebin on Wednesday.
That said, Rosenberg also added that “the fact that there are hooks in these events suggests that future versions may abuse this type of functionality, and CIQ should be held accountable and be under close scrutiny so that this type of privacy invasion does not occur. But all the recent noise on this is mostly unfounded.”
As for what the man who first accused Carrier IQ of tracking most user information in the first place with his video demo, Android researcher Trevor Eckhart — Well, he’s been conspicuously silent as of late. TPM has contacted him and is awaiting response.
But Bace has a theory on what he was doing in his video.
“I think that he is not familiar with the full array of functions required to assure the sound and cost effective operation of a carrier class network,” Bace said. “He also appears not to understand the difference between parameters that are recorded in device-local audit trails (not under the control of CarrierIQ) vs data that is exported from that device.”