The targets of the hackers who have broken into hundreds of Gmail accounts were high level government officials who are “known” public figures, says a system administrator who examined the innards of one of the compromised computers.
When a Google engineer highlighted the incident on the company’s blog on Wednesday, he also linked to a malware blog maintained by “Mila Parkour”, the pseudonym for a systems administrator who the company says helped them to uncover the scam.
Parkour says she prefers that her employer remain anonymous, but she tells TPM that she analyses malware “for fun” and that she posts her analyses on the web to spark off conversation and research. She says that Parkour is a false surname, so that people don’t associate her malware work with her employer.
Examples of some of the spoofed emails posted to Parkour’s blog show shows that the targets would receive emails from addresses that looked as if they were people they knew in the Department of State and the military.
In the case of the person she helped, the person realized that they were a target of a scam when they replied to the phony message.
“The person replied to the spoofed message, which went to the real person, who said that [the message] was not really from him,” Parkour said.
When asked how the hackers could have known who these officials correspond with, Parkour noted that they could have accessed information about the targets through compromised accounts of their associates, by examining their links through social networks, and by learning more about them through Google.
“At least some of them mentioned in the media … they are known people,” Parkour said in an e-mail message to TPM.
And in some cases the snooping went on for up to a year, she said.
Parkour said that such targeted attacks — known in the security industry as “phishing attacks” — aren’t unusual and that ones coming from China are very common.
“It was just very interesting because they managed to maintain full presence and use the account for a very long period, and forward all emails to their own account,” Parkour wrote. “I thought such a bold approach was unusual and unnerving.”
In this case, all of the target’s emails were being forwarded to the hacker’s account.
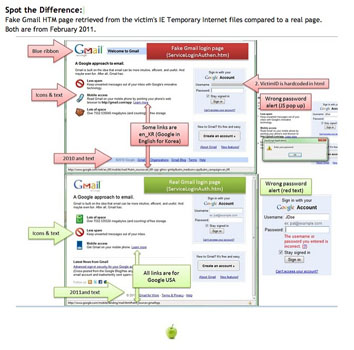
Recipients would be fooled into clicking on attachments because the emails looked as if they were from people the targets knew. But once they clicked on the attachments, the web page would take them to another page that looked as if it was the Gmail login page, making it look as if there had been a glitch and Gmail had kicked the user out by mistake.
The hackers would then harvest the user’s account login information once they tried to log in again at the phony page.
“I think an average senior official is likely to fall for it — I saw it happen,” Parkour wrote to TPM. “They know about targeted attacks and suspicious stuff, but when a message comes from someone with whom they talk [to] 20 times a day (spoofed and looks very plausible,) and talks about pics for the last weeks meeting, yes, they click to download.”
Some of the email examples on Parkour’s page are particularly intriguing because they look as if they were officials in the State Department who were preparing for Chinese President Hu Jintao’s visit to the United States back in January.
One of the titles of the emails, dated January 5, for example, says “Draft US-China Joint Statement.”
In a press conference Thursday, a Chinese government official denied having anything to do with the hacks, and China’s official news service Xinhau ran an editorial denouncing Google for undermining trust on the internet.
Underneath the editorial were two stories about Apple overtaking Google “as most valuable brand,” and Google subsidiaries being “probed for tax fraud.”
A spokesperson for Google declined to respond to the Chinese government’s statements, and an FBI spokesman said “We’re going to look into it with Google and other government agencies.”