Updated 2:29 pm ET, Wednesday, November 2
Microsoft has a big malware mess on its hands: A piece of malware targeting industrial infrastructure and systems manufacturers overseas, which has been called “nearly identical to Stuxnet,” by CrySyS, the Hungarian computer research lab that discovered the virus, exploits a previously unknown vulnerability in Microsoft Word to install itself, according to an update posted Tuesday by American cybersecurity company Symantec.
As Symantec’s Vikram Thakur explained on the company’s blog: “The installer file is a Microsoft Word document (.doc) that exploits a previously unknown kernel vulnerability that allows code execution…When the file is opened, malicious code executes and installs the main Duqu binaries.”
The phony Word document is emailed as an attachment to victims’ computers that bypasses antivirus software. Once downloaded, it also installs an “infostealer” that logs a user’s keystrokes and steals other system information, also replicating across secure networks using the passwords obtained by the keystroke logger and installing new copies of Duqu in shared folders. It is even able to penetrate secure networks by having secure servers communicate with infected machines and then out onto the public Internet, where the hacker can obtain all of the data. The malware is programmed to remain active for 30 days after which time it automatically removes itself.
But during the time the malware is active on an infected computer, “the attackers are looking for information such as design documents that could help them mount a future attack on various industries, including industrial control system facilities,” Symantec theorizes in a lengthier report on the threat. That approach is similar to the Stuxnet worm, which infected Iranian nuclear plant computers in late 2010, causing centrifuges at Iran’s uranium enrichment plant at Natanz to spin too fast, ruining up to 1,000 of them.
Stuxnet, like Duqu, takes advantage of Microsoft Windows security vulnerabilities.
Microsoft admitted to Reuters that Word was susceptible to the threat, as well as to the blog WinRumors shortly after Symantec published its report on Tuesday.
“We are working to address a vulnerability believed to be connected to the Duqu malware,” a Microsoft spokesperson told WinRumors, elaborating to Reuters that it was “working diligently to address this issue and will release a security update for customers.”
As of the time of this posting, no security update has been released on Microsoft’s security blogs. But the website Removemalwarespyware.com has posted a set of simple instructions on how to manually remove the malware.
Meanwhile, CrySyS, Symantec and other security companies are furiously trying to trace the origin of the threat and the location to where, and to whom, it is sending the data it steals.
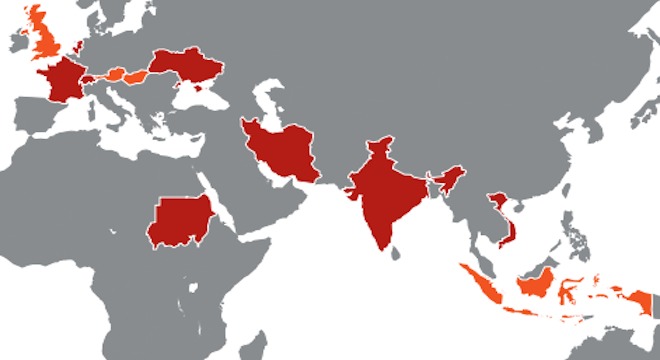
In it’s full report detailing the threat, Symantec writes that “infections have been confirmed in six organizations in eight countries,” including France, the Netherlands, Switzerland, Ukraine, India, Iran, Sudan and Vietnam. The company notes that other security vendors have reported infections in the United Kingdom, Australia, Hugary and Indonesia.
Symantec confirmed the discovery of the installer of the Duqu virus using data uncovered by CrySyS, Laboratory of Cryptography and System Security at the Budapest University of Technology and Economics, which first publicized its role in discovering the virus on October 21.
However, despite the claims from both Symantec, CrySyS and others that Duqu is extremely similar to Stuxnet (Symantec even theorizes it shares the same creators) Dell’s Secureworks isn’t so sure. As the company wrote on October 26:
All of the similarities from a software point of view are in the “injection” component implemented by the kernel driver. The ultimate payloads of Duqu and Stuxnet are significantly different and unrelated. One could speculate the injection components share a common source, but supporting evidence is circumstantial at best and insufficient to confirm a direct relationship. The facts observed through software analysis are inconclusive at publication time in terms of proving a direct relationship between Duqu and Stuxnet at any other level.
That assessment seems to be in the minority, though. Aleks Gostev, chief security expert at Russian cybersecurity company Kaspersky Lab, criticized SecureWorks on Twitter, saying he didn’t “understand why SecureWorks denies HUGE similarities in #Duqu and #Stuxnet.”
As Gostev wrote on Kapersky’s blog: “At the moment, the highest number of Duqu incidents have been recorded in Iran. This fact brings us back to the Stuxnet story and raises a number of issues,” later updating with a new post, adding “Our research shows that the incidents we detected involving Duqu in Sudan and Iran are actually bigger than initially thought.”
In any case, whoever created the worm, and whoever the designated target is, Microsoft sure has another tough security issue on its hands. We’ve reached out to the company for more information on how they are handling the threat and will update when they respond.
Late update: Microsoft responds with the following statement, emailed by Jerry Bryant, group manager, response communications, Microsoft Trustworthy Computing: “Microsoft is collaborating with our partners to provide protections for a vulnerability used in targeted attempts to infect computers with the Duqu malware. We are working diligently to address this issue and will release a security update for customers through our security bulletin process.”
We’ve reached back out to find out which partners Microsoft is collaborating with and where the security updates will be posted. Stay tuned.
Second late update: Microsoft will post its security updates related to Duqu here.